Navigation
- Common Setup
- Prowler Cloud Authentication
- Prowler CLI Authentication
- Supported PowerShell Versions
- Required PowerShell Modules
Common Setup
Authentication Methods Overview
Prowler Cloud uses app-only authentication. Prowler CLI supports the same app-only options and two delegated flows. Prowler Cloud: Prowler CLI:- Application Certificate Authentication (Recommended)
- Application Client Secret Authentication
- Azure CLI Authentication
- Interactive Browser Authentication
Required Permissions
To run the full Prowler provider, including PowerShell checks, two types of permission scopes must be set in Microsoft Entra ID.Application Permissions for App-Only Authentication
When using service principal authentication, add these Application Permissions: Microsoft Graph API Permissions:AuditLog.Read.All: Required for Entra service.Directory.Read.All: Required for all services.Policy.Read.All: Required for all services.SharePointTenantSettings.Read.All: Required for SharePoint service.
Exchange.ManageAsAppfrom external APIOffice 365 Exchange Online: Required for Exchange PowerShell module app authentication. TheGlobal Readerrole must also be assigned to the app.application_accessfrom external APISkype and Teams Tenant Admin API: Required for Teams PowerShell module app authentication.
Directory.Read.All can be replaced with Domain.Read.All for more restrictive permissions, but Entra checks related to DirectoryRoles and GetUsers will not run. If using this option, you must also add the Organization.Read.All permission to the application registration for authentication.These permissions enable application-based authentication methods (client secret and certificate). Using certificate-based authentication is the recommended way to run the full M365 provider, including PowerShell checks.
Browser Authentication Permissions
When using browser authentication, permissions are delegated to the user, so the user must have the appropriate permissions rather than the application.Step-by-Step Permission Assignment
Create Application Registration
-
Access Microsoft Entra ID.

-
Navigate to “Applications” > “App registrations”.
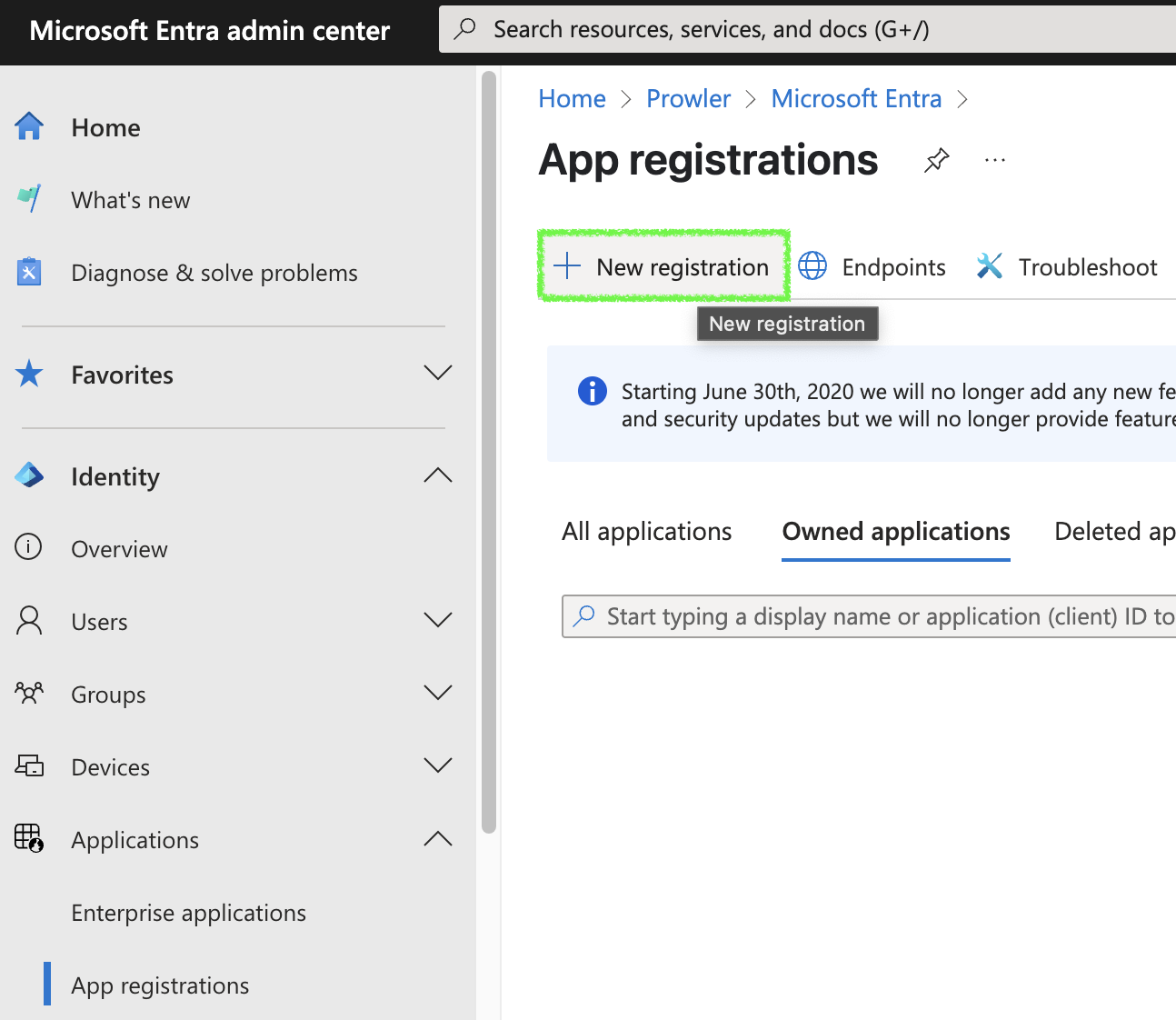
-
Click ”+ New registration”, complete the form, and click “Register”.
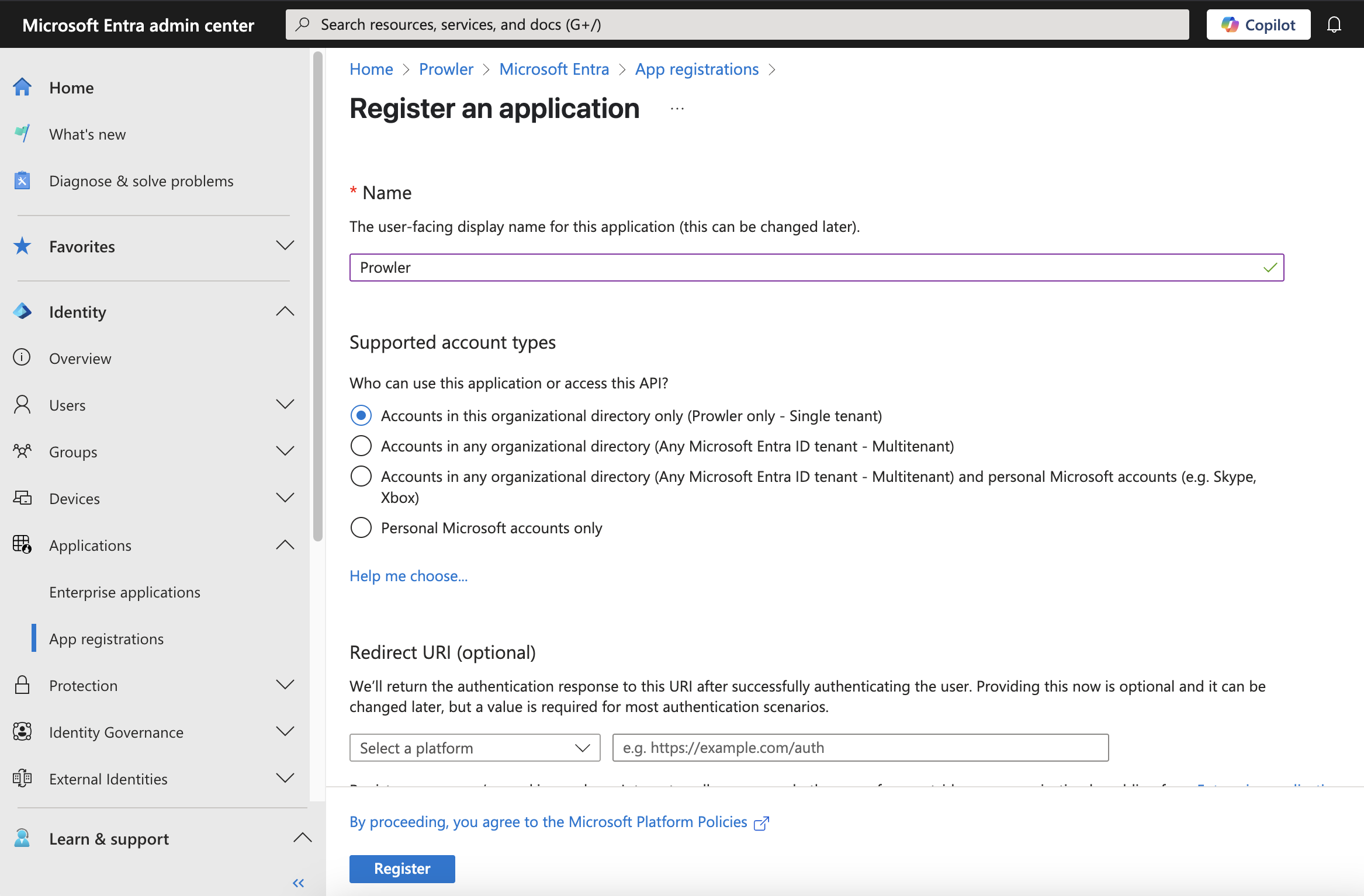
-
Go to “Certificates & secrets” > “Client secrets” > ”+ New client secret”.
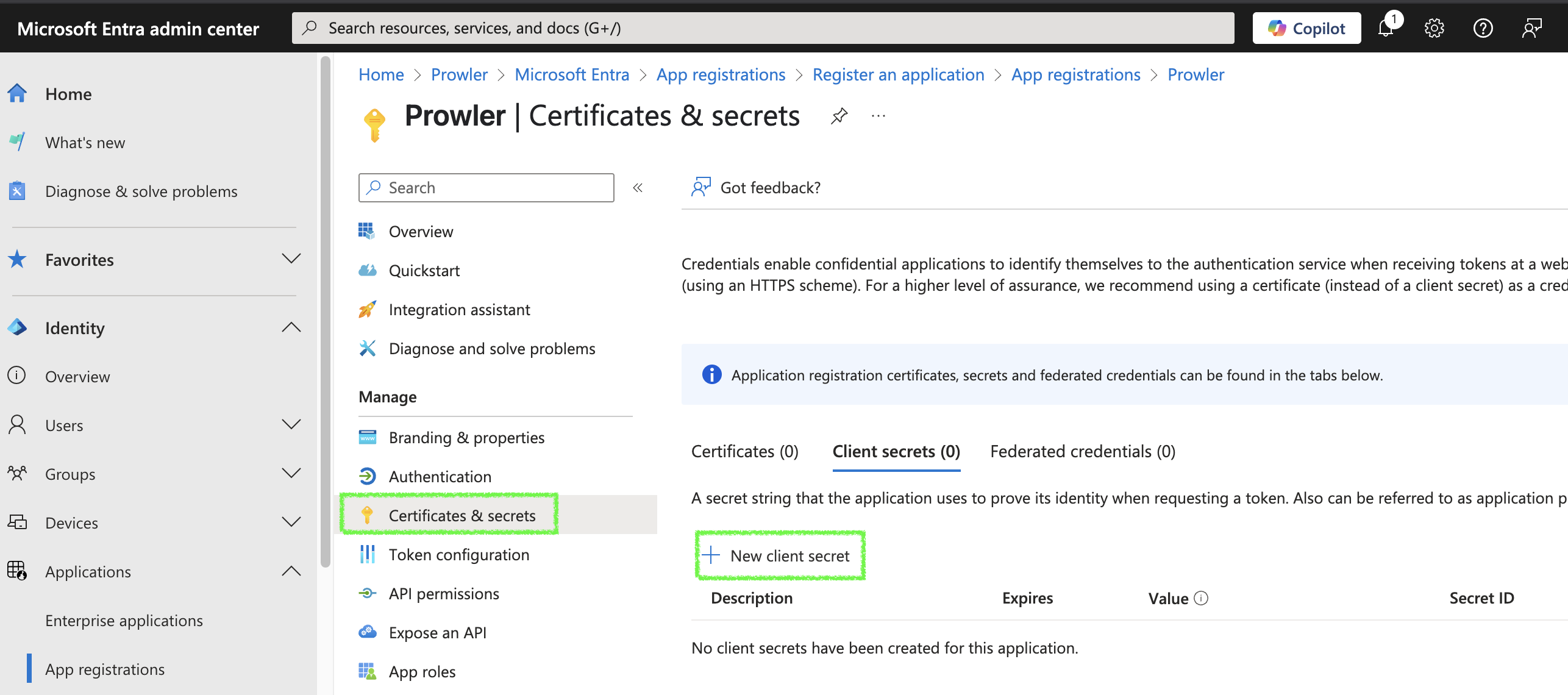
-
Fill in the required fields and click “Add”, then copy the generated value (this will be
AZURE_CLIENT_SECRET).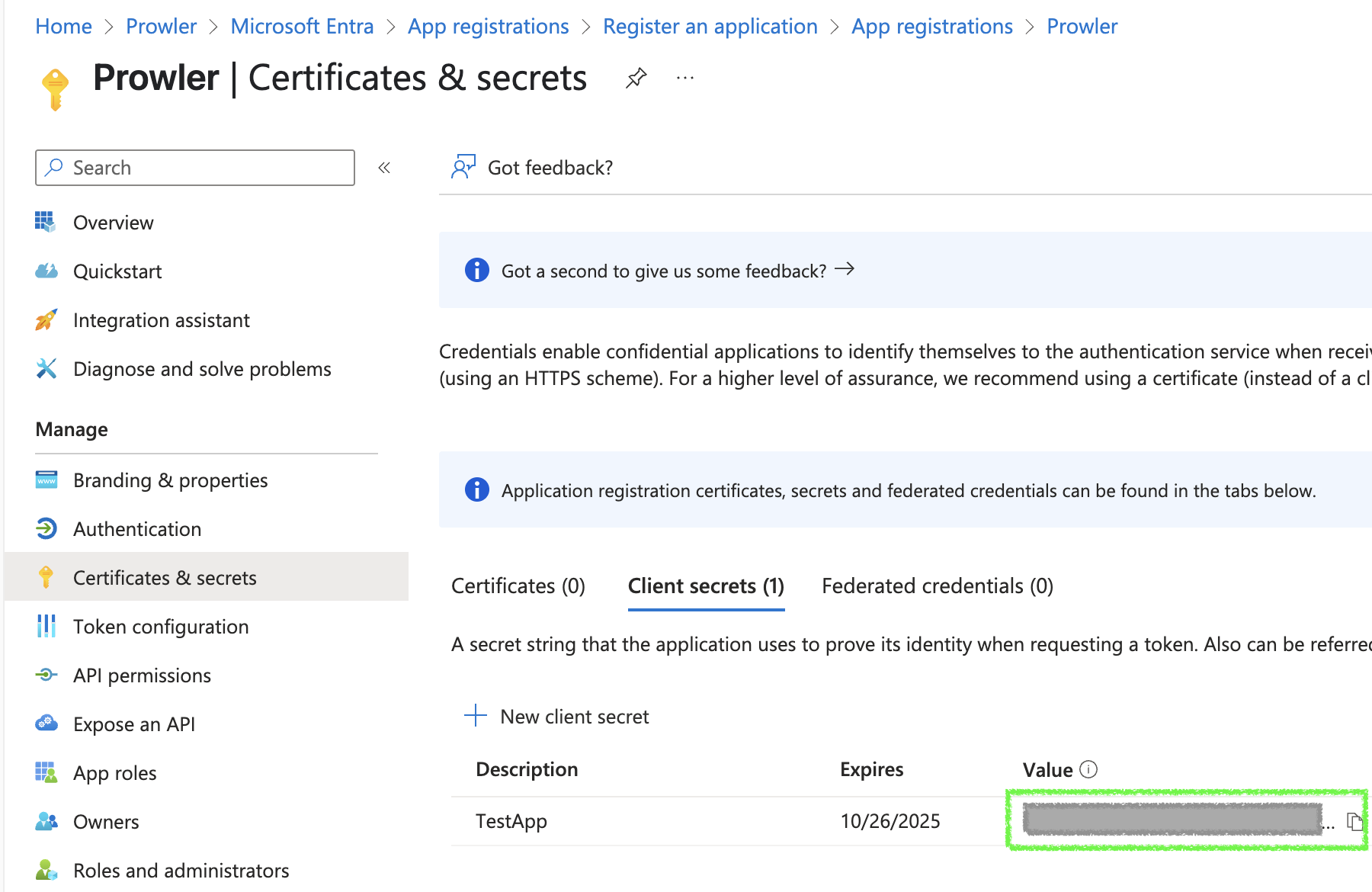
Grant Microsoft Graph API Permissions
-
Open API permissions for the Prowler application registration.
-
Click ”+ Add a permission” > “Microsoft Graph” > “Application permissions”.
-
Search and select the required permissions:
AuditLog.Read.All: Required for Entra serviceDirectory.Read.All: Required for all servicesPolicy.Read.All: Required for all servicesSharePointTenantSettings.Read.All: Required for SharePoint service

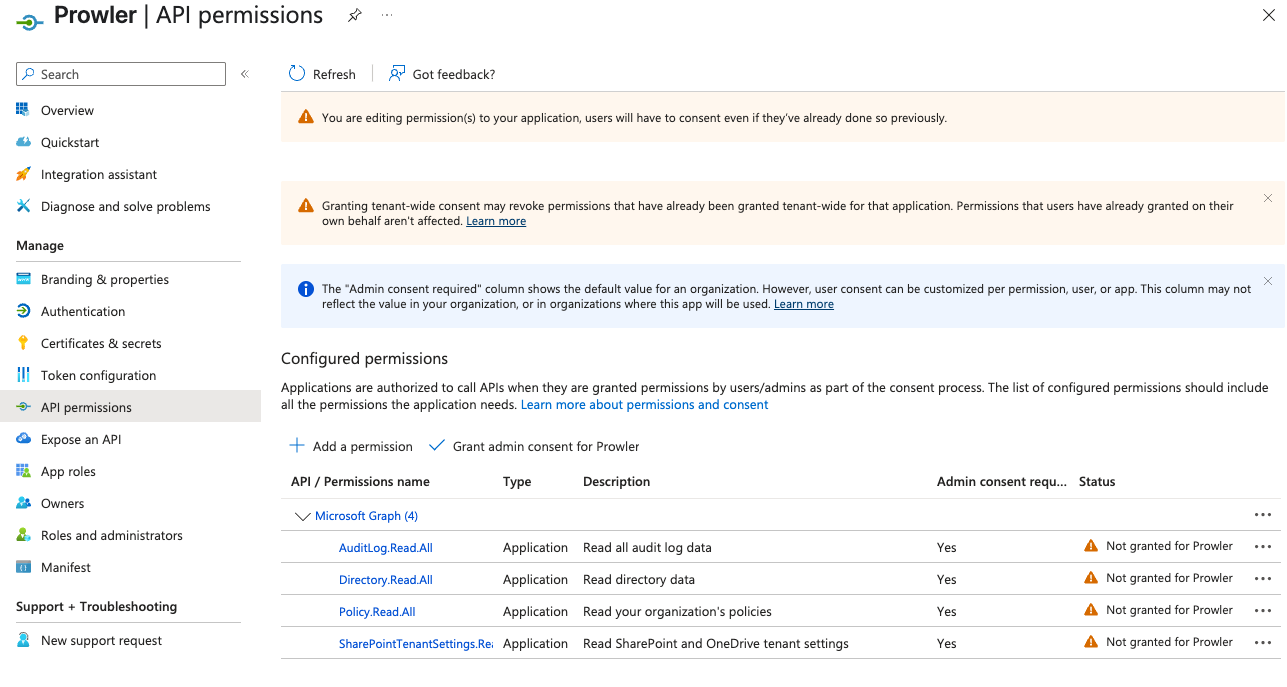
-
Click “Add permissions”, then click “Grant admin consent for
<your-tenant-name>”.
Grant PowerShell Module Permissions
-
Add Exchange API:
- Search and select “Office 365 Exchange Online” API in APIs my organization uses.
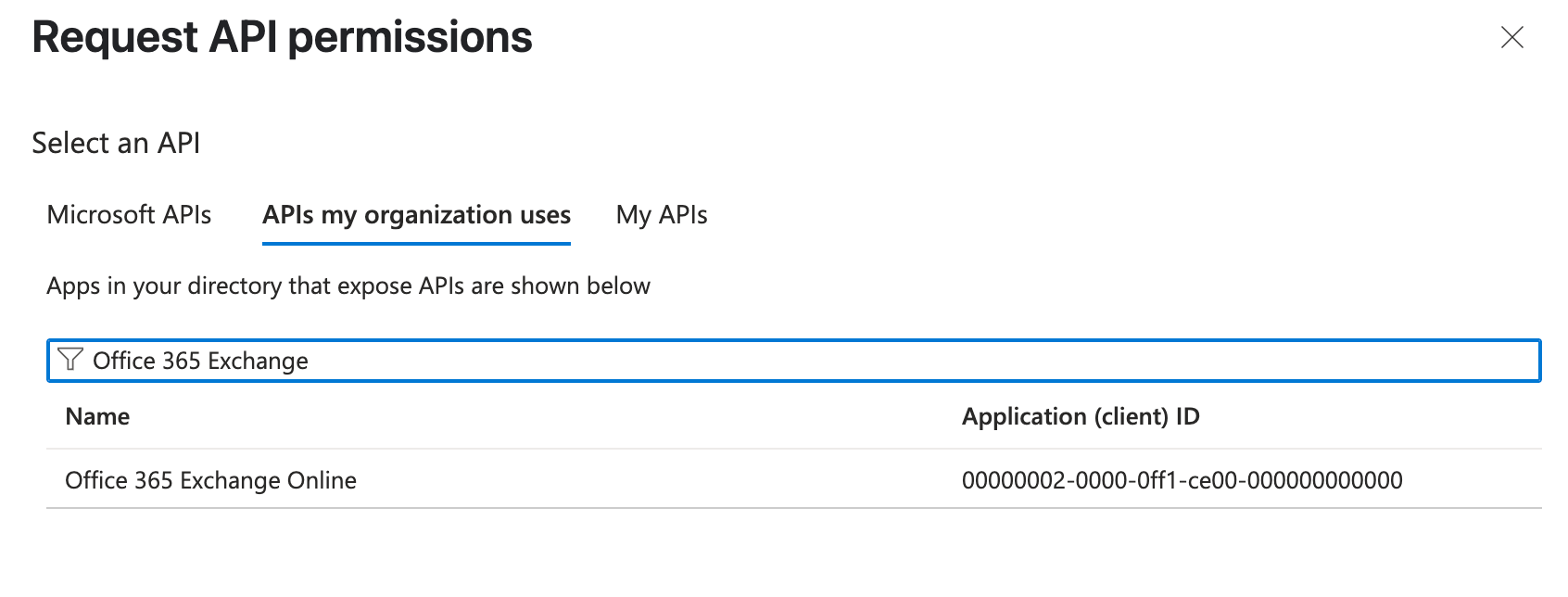
- Select “Exchange.ManageAsApp” permission and click “Add permissions”.
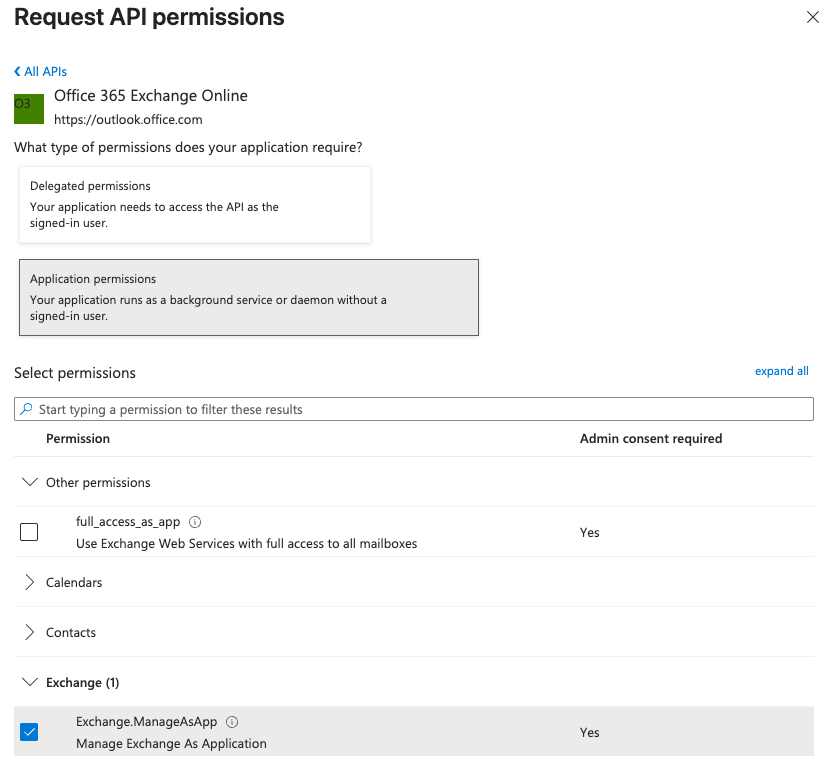
- Assign
Global Readerrole to the app: Go toRoles and administrators> clickherefor directory level assignment.
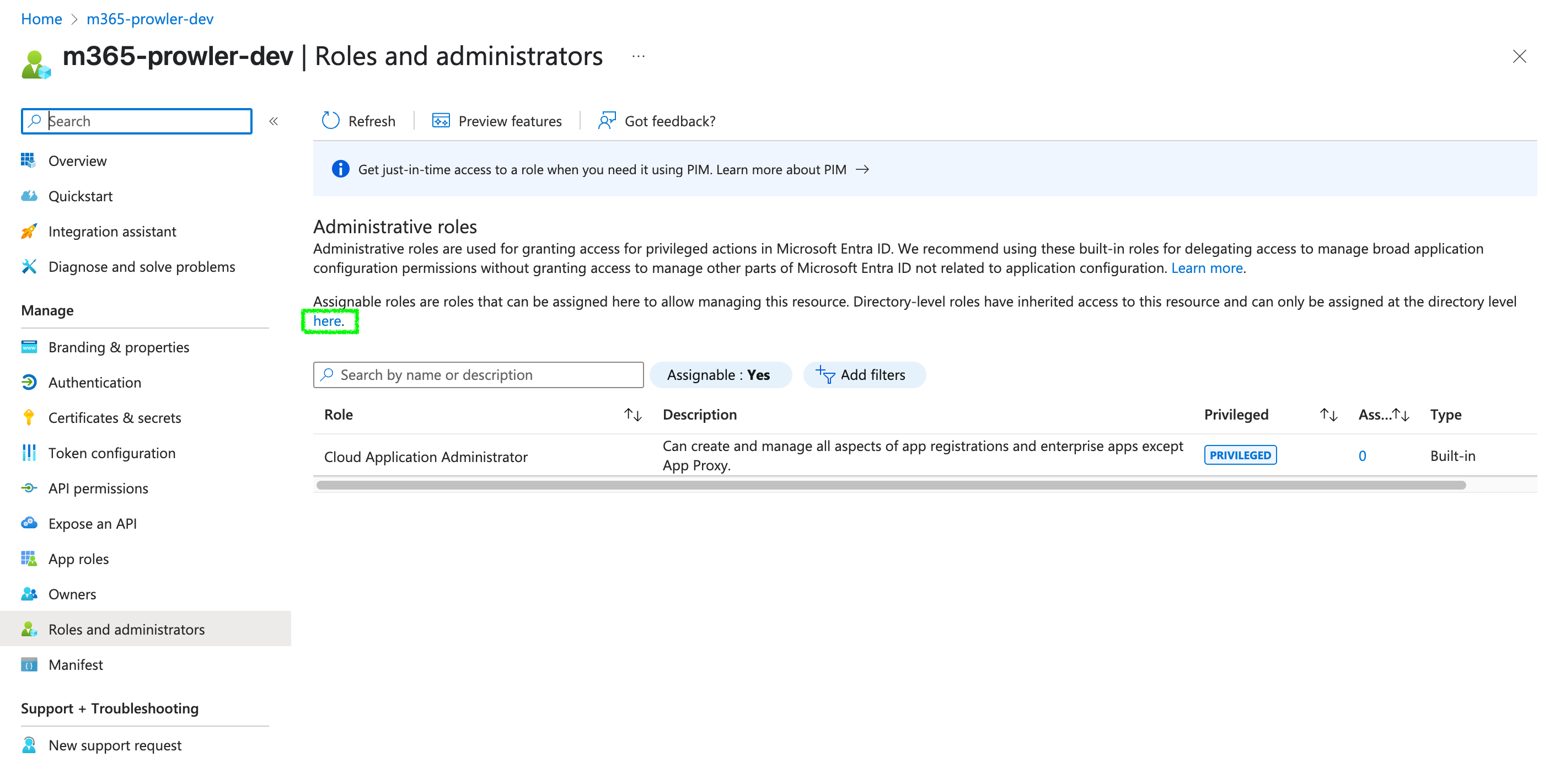
- Search for
Global Readerand assign it to the application.

-
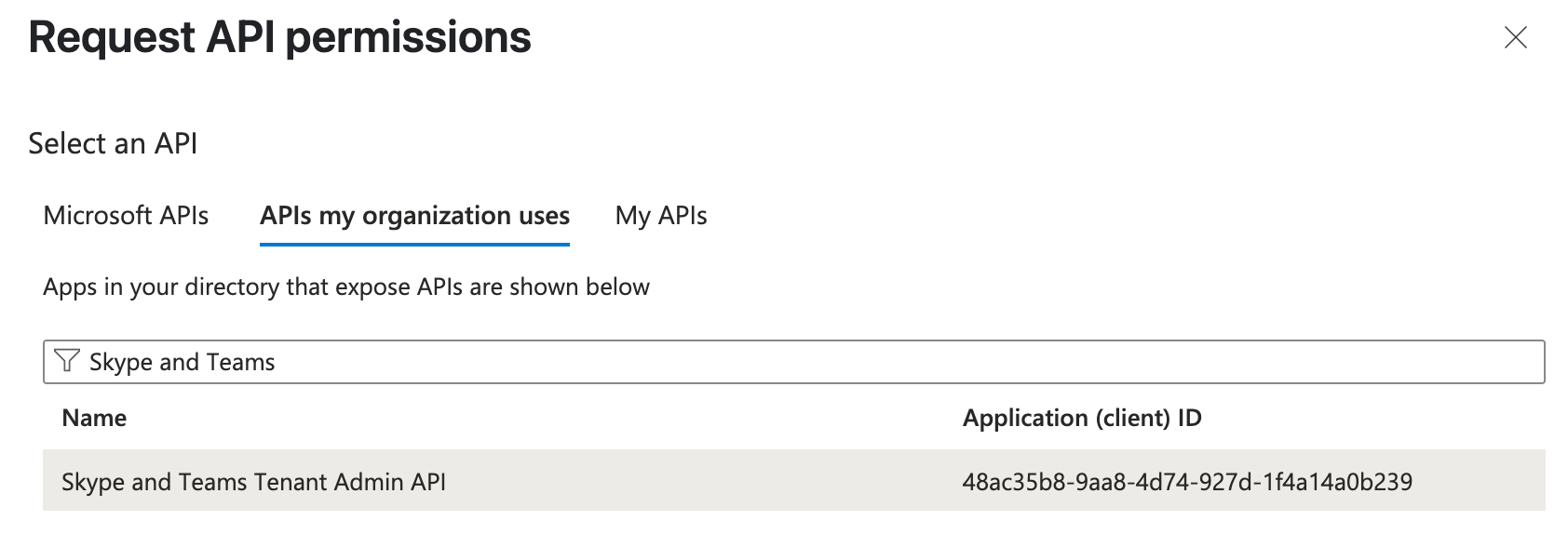
Add Teams API:
- Search and select “Skype and Teams Tenant Admin API” in APIs my organization uses.
- Select “application_access” permission and click “Add permissions”.
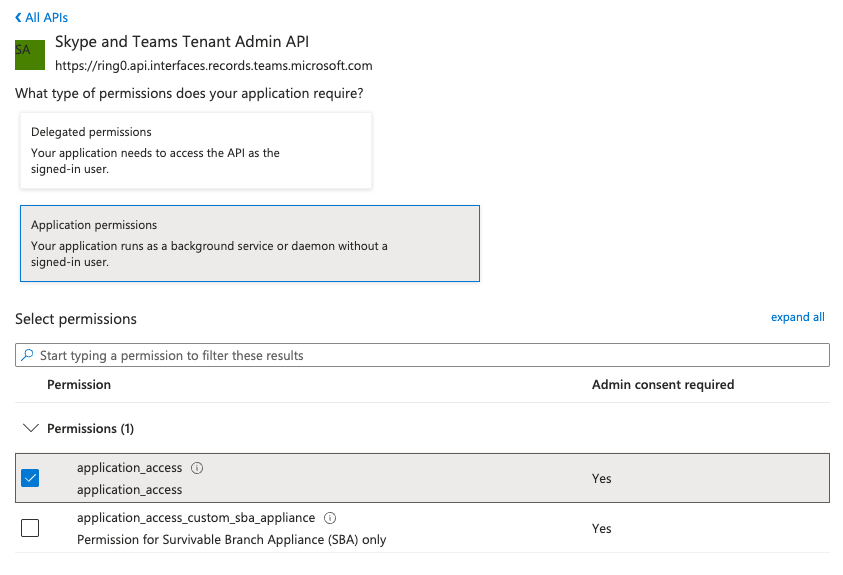
-
Click “Grant admin consent for
<your-tenant-name>” to grant admin consent.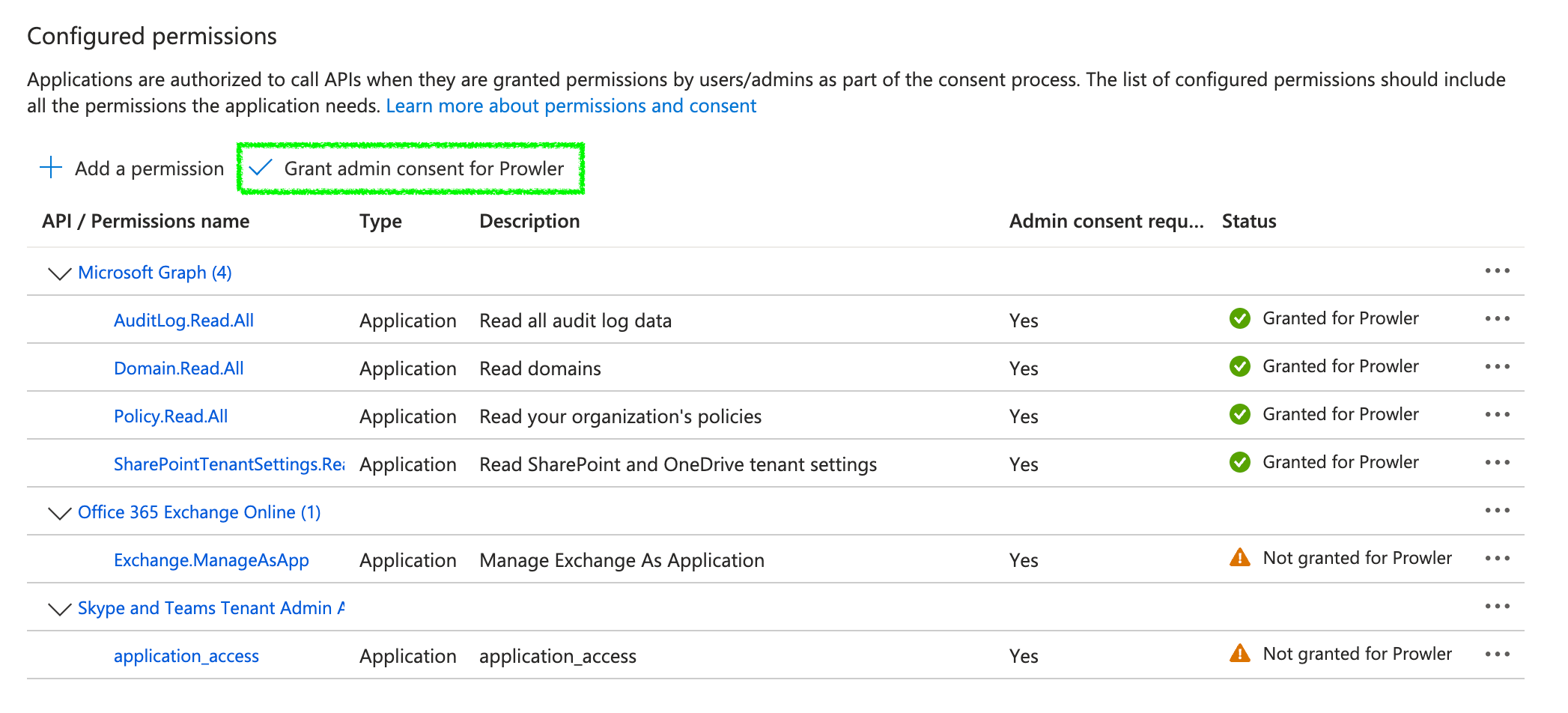
Application Certificate Authentication (Recommended)
Available for both Prowler Cloud and Prowler CLI Authentication flag for CLI:--certificate-auth
Certificate-based authentication replaces the client secret with an X.509 certificate that signs Microsoft Entra ID tokens for the Prowler application registration.
This is the recommended approach for production environments because it avoids long-lived secrets, supports the full provider (including PowerShell checks), and simplifies unattended automation. Microsoft also recommends certificate credentials for app-only access, see Manage certificates for applications.
Generate the Certificate
The service principal needs a certificate that contains the private key locally (for Prowler) and the public key uploaded to Microsoft Entra ID. The following commands show a secure baseline workflow on macOS or Linux using OpenSSL:Upload the Certificate to Microsoft Entra ID
- Open Microsoft Entra ID > App registrations > the Prowler application.
- Go to Certificates & secrets > Certificates.
- Select Upload certificate and choose
prowlerm365.cer. - Confirm the certificate appears with the expected expiration date.
prowlerm365.pfx.b64) for the next step.
Provide the Certificate to Prowler
- Prowler Cloud: Paste the Base64-encoded PFX in the
certificate_contentfield when configuring the Microsoft 365 provider in Prowler Cloud. - Prowler CLI: Export credential variables or pass the local file path when running Prowler.
AZURE_CLIENT_ID and AZURE_TENANT_ID in the environment when --certificate-path is used.
Do not mix certificate authentication with a client secret. Provide either a certificate or a secret to the application registration and Prowler configuration.
Application Client Secret Authentication
Available for both Prowler Cloud and Prowler CLI Authentication flag for CLI:--sp-env-auth
Authenticate using a Microsoft Entra application registration with a client secret by configuring the following environment variables:
--sp-env-auth will fail. This workflow is helpful for initial validation or temporary access. Plan to transition to certificate-based authentication to remove long-lived secrets and keep full provider coverage in unattended environments.
To scan every M365 check, ensure the required permissions are added to the application registration. Refer to the PowerShell Module Permissions section for more information.
Prowler Cloud Authentication
Use the shared permissions and credentials above, then complete the Microsoft 365 provider form in Prowler Cloud. The platform persists the encrypted credentials and supplies them during scans.Application Certificate Authentication (Recommended)
- Select Application Certificate Authentication.
- Enter the tenant ID and application (client) ID.
- Paste the Base64-encoded certificate content.
Application Client Secret Authentication
- Select Application Client Secret Authentication.
- Enter the tenant ID and application (client) ID.
- Enter the client secret.
Prowler CLI Authentication
Certificate Authentication
Authentication flag for CLI:--certificate-auth
After credentials are exported, launch the Microsoft 365 provider with certificate authentication:
Client Secret Authentication
Authentication flag for CLI:--sp-env-auth
After exporting the secret-based variables, run:
Azure CLI Authentication
Authentication flag for CLI:--az-cli-auth
Azure CLI authentication relies on the identity that is already signed in with the Azure CLI. Before running Prowler, make sure you have an active CLI session in the target tenant:
Interactive Browser Authentication
Authentication flag for CLI:--browser-auth
Authenticate against Azure using the default browser to start the scan. The --tenant-id flag is also required.
These credentials only enable checks that rely on Microsoft Graph. The entire provider cannot be run with this method. To perform a full M365 security scan, use the recommended authentication method.
Since this is a delegated permission authentication method, necessary permissions should be assigned to the user rather than the application.
Supported PowerShell Versions
PowerShell is required to run certain M365 checks. Supported versions:- PowerShell 7.4 or higher (7.5 is recommended)
Why Is PowerShell 7.4+ Required?
- PowerShell 5.1 (default on some Windows systems) does not support required cmdlets.
- Older cross-platform PowerShell versions are unsupported, leading to potential errors.
Installing PowerShell is only necessary if you install Prowler via pip or other sources. SDK and API containers include PowerShell by default.
Installing PowerShell
Installing PowerShell is different depending on your OS:- Windows
- MacOS
- Linux (Ubuntu)
- Linux (Alpine)
- Linux (Debian)
- Linux (RHEL)
- Docker
Required PowerShell Modules
Prowler relies on several PowerShell cmdlets to retrieve necessary data. These cmdlets come from different modules that must be installed.Automatic Installation
The required modules are automatically installed when running Prowler with the--init-modules flag.
Example command:
Prowler installs the modules using
-Scope CurrentUser.
If you encounter any issues with services not working after the automatic installation, try installing the modules manually using -Scope AllUsers (administrator permissions are required for this).
The command needed to install a module manually is:Modules Version
- MSAL.PS: Required for Exchange module via application authentication.
- ExchangeOnlineManagement (Minimum version: 3.6.0) Required for checks across Exchange, Defender, and Purview.
- MicrosoftTeams (Minimum version: 6.6.0) Required for all Teams checks.

